Development
See also:
OAuth & OIDC
Basics
OpenID Foundation
How OpenID Connect Works - OpenID Foundation
What is OpenID Connect OpenID Connect is an interoperable authentication protocol based on the OAuth 2.0 framework of specifications (IETF RFC 6749 and 6750). It simplifies the way to verify the identity of users based on the authentication performed by an Authorization Server and to obtain user profile information in an interoperable and REST-like manner.OpenID

Okta Developer
An Illustrated Guide to OAuth and OpenID Connect
An illustrated guide to explain OAuth and OpenID Connect!
Tutorials
OAuth from First Principles - Stack Auth
Stack Auth is the open-source Auth0 alternative. We are your login and signup page, and everything that comes with that.

Roman Glushko
What's OAuth2 Anyway? - Blog by Roman Glushko
Why the OAuth2 protocol was designed the way it is and how it works.

A simple OpenID connect tutorial — /var/
Best Practice
The Copenhagen Book
OAuth
A basic guideline on implementing auth for the web.
OAuth2 - OWASP Cheat Sheet Series
Website with the collection of all the cheat sheets of the project.
Weird & Leaf
Muni Blog
Capabilities & Identity with Leaf
Recently Christine Lemmer-Webber shared her 'recipe for the fediverse'. Let's see whether Leaf can meet her requirements.
Polyproto & Federation ID
Transforming Online Communication | polyproto
The polyproto federation protocol

AT Protocol auth & did:plc
Bluesky
A Self-Authenticating Social Protocol - Bluesky
Bluesky’s mission is to drive the evolution from platforms to protocols. The conceptual framework we've adopted for meeting this objective is the "self-authenticating protocol."
OAuth for AT Protocol | Bluesky
We are very happy to release the initial specification of OAuth for AT Protocol! This is expected to be the primary authentication and authorization system between atproto client apps and PDS instances going forward, replacing the current flow using App Passwords and createSession over time.

AT Protocol
OAuth - AT Protocol
OAuth for Client/Server Authentication and Authorization
AT Protocol
Identity - AT Protocol
How the AT Protocol handles user identity.
Decentralized Identifiers (DIDs)
SpruceID
Upgradeable Decentralized Identity - DID Method Traits
DID method traits are testable properties about DID methods that can help implementers tame complexity and choose the right DID method(s) for their use case.
Decentralized Identifiers (DIDs) v1.0
Decentralized identifiers (DIDs) are a new type of identifier that enables verifiable, decentralized digital identity. A DID refers to any subject (e.g., a person, organization, thing, data model, abstract entity, etc.) as determined by the controller of the DID. In contrast to typical, federated identifiers, DIDs have been designed so that they may be decoupled from centralized registries, identity providers, and certificate authorities. Specifically, while other parties might be used to help enable the discovery of information related to a DID, the design enables the controller of a DID to prove control over it without requiring permission from any other party. DIDs are URIs that associate a DID subject with a DID document allowing trustable interactions associated with that subject.
Medium - https://medium.com/@oliver.terbu
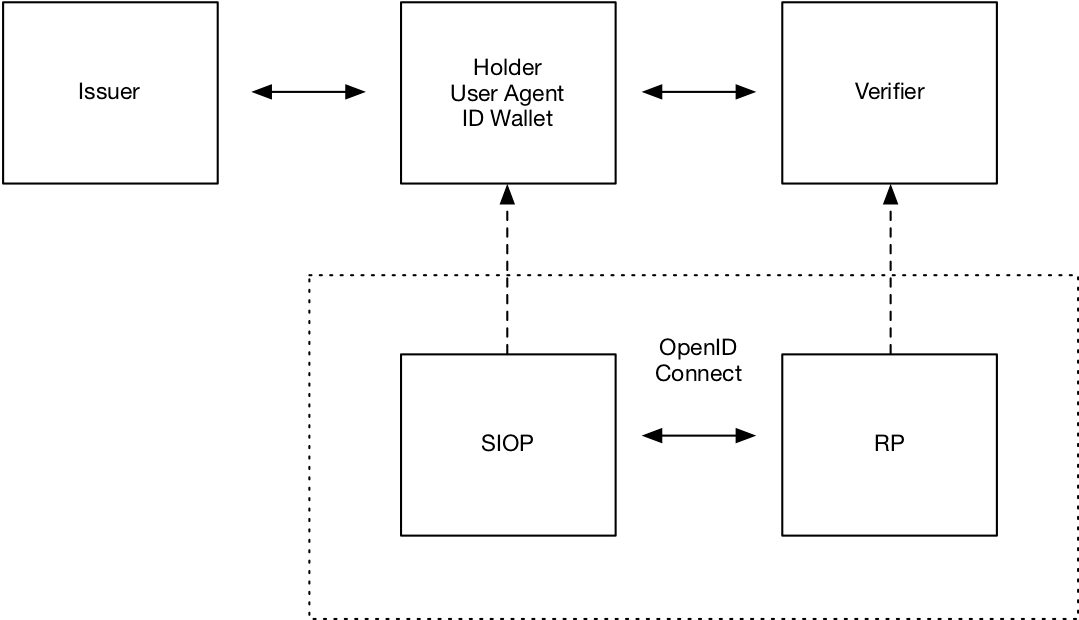
Using OpenID Connect with Decentralized Identifiers
The DID Auth WG chaired by myself had its kickoff meeting on April 25th. As DID Auth has different interpretations, the group defined that…
Codeberg.org
FedID
An online representation of you, that you own and control.
Domain-based Usernames
DNS Account Handles, A Whitepaper
A proposal for use of DNS names to support universal account identifiers 'handles' is described. Once registered, a handle may be used for authentication to any network service, to initiate communication with the holder or as the basis for IoT device management. This document is a whitepaper proposing the general approach. A strawman prototype supporting single account Web login across multiple sites, onboarding of IoT devices and end to end secure messaging, file-drop, voice and video and has been built using existing and proposed IETF work.
IETF Datatracker - N. Johnson
Integration of DNS Domain Names into Application Environments: Motivations and Considerations

Introduction to did:webvh - did:webvh DID Method Information -- "did:web + Verifiable History"
Other
The Path to Decentralized Identity in ActivityPub
